LanSchool
From Compsci.ca Wiki
Hacker Dan (Talk | contribs) m |
(→Communications with LanSchool) |
||
| (23 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | [[ | + | '''NOTE:''' This page details a proof of concept exploit of the LanSchool program '''which no longer works''' (since versions 7.0 and up). CompSci.ca and [[Hacker Dan]] do not support, condone or recommend the use of it in real life (So don't send us e-mails asking how to get it working or how to hack your schools network). Also since this exploit was found and LanSchooled was created, '''LanSchool has fixed the potential security hole described on this page'''. CompSci.ca and [[Hacker Dan]] will not help you exploit new versions of the software so do not e-mail us asking how. All information is provided as is and is the sole option of Hacker Dan and we are by no means responsible for how you use it or the effects it may have on you, your computer or anything that happens to you as a result of reading this page or using the software on and linked to from it. |
| + | |||
| + | '''Disclaimer:''' The content of this page is only the opinion of Hacker Dan and those who edit its content. Nothing on this page should be taken as fact with out checking the validity of the claim. | ||
| + | |||
==What is LanSchool== | ==What is LanSchool== | ||
| - | LanSchool is | + | [[Image:Taskbar.JPG|thumb|What it looks like]] |
| + | LanSchool is type of monitoring program that is used by many school boards in Ontario to keep an eye on their students as well as controlling one or all computers in a given lab. It is seen by some as another example of the school boards spending money on software that they could get for free, with the free version even being of higher quality. Early versions LanSchool had a critical flaw in its design which caused the security hole mentioned below (which is now fixed in versions 7.0 and up). | ||
<br><br> | <br><br> | ||
| - | The LanSchool website: http://www.lanschool.com | + | The LanSchool website: http://www.lanschool.com/ |
<br><br> | <br><br> | ||
| + | |||
| + | |||
==The Story== | ==The Story== | ||
| - | The Story as | + | '''Note:''' LanSchool has since updated there software and fixed the security issue talked about on this page in the below story. '''The bellow is solely the opinion of Hacker Dan''' and should not be taken as anything but just that. |
| - | + | ||
| - | + | ||
| + | The Story as told by [[Hacker Dan]]: | ||
<br><br> | <br><br> | ||
| - | + | During Grade 12, I changed schools, and the new school that I went to had substantially better computing facilities. I thought this was a good thing, but after playing around for a bit, I noticed a little green icon in the system tray that did not seem to do anything. Looking in to this, I found out that it was a program named LanSchool (http://www.lanschool.com/). What is LanSchool you ask? The name makes it sound innocent enough, maybe something to help students? Well, it may have started out that way but what it has become is basically a Trojan horse program for teachers to use to watch everything that you are doing (inducing watching your screen) as well as giving them the ability to control your computer or all computers in the lab at the same time. As usual, the school board decided to spend money on something they could get for free and got a crappier version than what they could have got for free. | |
<br><br> | <br><br> | ||
| - | So | + | So I started looking in to LanSchool more and found a demo version on their site. This demo version could not interact with real versions that the school used and would not allow students to do any damage. 1st, I looked in to how it used the registry of the computers that it was on, and found that every time the teacher application sent a command to the student versions it recorded which windows user sent the command, the computer name of the computer that they were on and the time in all registries of every computer on the network. This meant that finding a full version of the software, although not hard, would end you up in a lot of trouble unless you brought your own computer to school and even then still could. |
<br><br> | <br><br> | ||
| - | + | So I began to look at the packets it was sending and to my shock they were UDP and not TCP and they had no encryption or coding to them at all. This means that it is extremely easy to spoof the packets. So I quickly wrote up a simple java program to test out my theory. After some time and experimentation, I decoded what most of the packets meant and was able to control the demo version of LanSchool. After looking more at the packets, I noticed that the differences between the demo version and the real version was that the demo version uses only one channel that is never used by the real version. So it was simple a matter of changing the channel byte to a real channel in the packet to get it to work with most, if not all, versions of LanSchool. Also this allowed me to make the registry logs say what ever I wanted, including blaming other students for the hack. | |
<br><br> | <br><br> | ||
| - | It is now almost 2 years | + | Now being the nice guy that I am, I emailed my findings to LanSchool and suggested several ways to fix this exploit. There responses basically said that they would rather spend their time and effort enforcing the rules of the school and the law than fixing their program. They even made threats of legal action as well as suspensions that I could get were I to use this program. So next, I went to my school and actually demonstrated (with their permission) the exploit and how insecure the product was. Again, nothing happened as a result of my efforts, so a month later, I published how the system worked on compsci.ca. |
| + | <br><br> | ||
| + | It is now almost 2 years later, so I have rewritten my hack so anyone, even script kiddies can use it, even with a nice GUI and everything. My hope is that by doing this, I will teach people why programming software in the same way that LanSchool has been written is bad from a security and integrity viewpoint and to encourage the school board to buy (if they must use such software) better software from companies that know what they are doing and are willing to keep with the times. BTW, LanSchools website still claims that there are no known bugs with LanSchool. | ||
| + | <br><br> | ||
| + | '''Update:''' LanSchool fixed the security issue on May of 2007 and tried to contact Hacker Dan at this time, however due to a mix up with e-mail addresses this news was not received in till August 2008. | ||
<br><br><br> | <br><br><br> | ||
| + | |||
| + | ==Communications with LanSchool== | ||
| + | ===Feb. 26th, 2006=== | ||
| + | To: LanSchool<br> | ||
| + | From: [[Hacker Dan]]<br> | ||
| + | <table border="1"><tr><td> | ||
| + | Hello, I am writing to let you know that you have a security flaw in your software, LanSchool v6.5. As with past versions of LanSchool, the system is not secure and uses a communication mechanism that allows for manipulation by anybody on a network whether they have the teacher version of the software installed or not. This becomes even more concerning when you see that this allows the exploiter to manipulate logs that are stored in the registry to what ever they want by manipulating communication appropriately. This would allow some students to exploit the network and then make it look like another student committed the attack from what ever computer they chose. | ||
| + | <br><br> | ||
| + | Also the scope of this exploit would go beyond affecting one computer or on lab at a time. With a little thought the exploiter could affect all computers in a school running the software by rotating threw the channels. Or even worse, the attack vector could be used to affect all LanSchool installs on the network that are not protected by a firewall. | ||
| + | <br><br> | ||
| + | My recommendation would be to add some level of security to the UDP packets used to communicate to the computers, like a password that is encrypted (through the use of a digest hashing algorithm, such as MD5) and then validate it on the client end agent using a password that it has been installed with. This would make the system as secure as the password and associated storage mechanism and encryption and would only require the installer of the software to add in one more text field. You could still use the UDP protocol with minimal modification to your code. | ||
| + | </td></tr></table> | ||
| + | |||
| + | |||
| + | ===May of 2007=== | ||
| + | LanSchool tried to contact Hacker Dan when version 7.0 was released and fixed the security hole, however the messages never made it to him due a mix up with e-mail addresses. | ||
| + | |||
| + | |||
| + | ===August 5th, 2008=== | ||
| + | Beliving that Hacker Dan has ignored there messages in 2007, LanSchool sent the fallowing legal threat to CompSci.ca: | ||
| + | http://compsci.ca/blog/wp-content/uploads/2008/08/lt-d-servos.pdf | ||
| + | |||
| + | [[Tony]], posted a copy of the letter to the CompSci.ca blog with his commentary: | ||
| + | http://compsci.ca/blog/lanschool-threatens-compscica-with-legal-actions/ | ||
| + | |||
| + | |||
| + | ===August 5th to 7th=== | ||
| + | Internet drama ensues as the blog post makes Reddit and users and friends of CompSci.ca E-mail LanSchool. | ||
| + | |||
| + | |||
| + | ===August 7th, 2008=== | ||
| + | Hacker Dan and CompSci.ca send there official reply: | ||
| + | http://compsci.ca/~dan/LT%20Dana%20Doggett.pdf | ||
| + | |||
| + | Dana Doggett of LanSchool replys: | ||
| + | <table border="1"><tr><td> | ||
| + | Dan, | ||
| + | |||
| + | |||
| + | |||
| + | I’m glad I’m finally talking to you directly. I’m assuming my older e-mails must have gone to a bad address. Data Stream Encryption was one of the main features of LanSchool v7.0 in May of 2007. I e-mailed you when that shipped but I guess it never got through. I feel confident that if we had been able to communicate better, this would never have gone this far. | ||
| + | |||
| + | |||
| + | |||
| + | I’m fine with the four points you listed in your letter, with one modification. Since I fixed this in v7.0 of LanSchool I would like #2 to state that the “potential security flaw” was fixed in v7.0. Since I added that feature specifically for you, I don’t see that as too much to ask. | ||
| + | |||
| + | |||
| + | |||
| + | If you will agree to that clarification, we will instruct our attorney that the issue has been resolved. | ||
| + | |||
| + | |||
| + | |||
| + | My background is in programming, not public relations. I’ve obviously handled this poorly. Were I able to re-run this entire scenario, I would have been MUCH more proactive from the very start. Please accept my apologies and know that when this sort of thing occurs in the future, hopefully I’ll have learned and do it better. | ||
| + | |||
| + | |||
| + | |||
| + | Sincerely, | ||
| + | |||
| + | Dana Doggett | ||
| + | </td></tr></table> | ||
| + | |||
| + | CompSci.ca makes the changes. | ||
| + | |||
| + | |||
| + | Hacker Dan's reply: | ||
| + | |||
| + | <table border="1"><tr><td> | ||
| + | The changes (with your modification to #2) have been made to the pages in question. Also tony will be updating his blog post, stating that the issue has been resolved and was likely due to a miscommunication, in the next few days. | ||
| + | |||
| + | If i had know of your attempts to contact me, i would have likely suggested and made the changes at that time. | ||
| + | |||
| + | I am glad this matter could be resolved reasonably with an agreement by both sides and i hope any dealings between us in the future will be positive. | ||
| + | |||
| + | Sincerely, | ||
| + | Dan | ||
| + | </td></tr></table> | ||
| + | |||
| + | |||
| + | ===August 19th, 2008=== | ||
| + | [[Tony]], after finishing his exams, finally writes a followup post to the above. http://compsci.ca/blog/legal-status-update/ | ||
| + | <br><br><br> | ||
| + | |||
==The Packet== | ==The Packet== | ||
| - | This is what the packet looks like: | + | '''Note:''' Lanschool's packet was changed in v7.0 in May 2007 and added Data Stream Encryption which fixed the potential security flaw. |
| + | |||
| + | |||
| + | This is what the UDP packet looks like: | ||
<br><br> | <br><br> | ||
| - | '''Mode | Version | Channel | + | '''Mode | Version | Channel |00 or DF |DA | D1| ___data here__|__log info__|''' |
<br><br> | <br><br> | ||
| - | Mode is | + | Mode is basically the command that you are send. So far, I have found a lot of them. Here are some examples: |
<br><br> | <br><br> | ||
| - | *00 - | + | *00 - Start broadcast of screens |
| - | *04 - | + | *04 - Restore computer screens |
| - | *07 - | + | *07 - Black all screens |
| - | *08 - | + | *08 - Unload Lanschool or just make it lock. |
<br><br> | <br><br> | ||
| - | The verson | + | The verson corresponds to the verson of Lanschool that you are running. Versons 5.x seem to like 01, 02 seems to be for 6.x |
<br><br> | <br><br> | ||
| - | The channel area is prity simple, it is the channel number. The demo verson uses channel FF in hex or 255 in | + | The channel area is prity simple, it is the channel number. The demo verson uses channel FF in hex or 255 in decimal. |
<br><br> | <br><br> | ||
| - | The next 3 bytes are kind of hard to figgure out but seem to | + | The next 3 bytes are kind of hard to figgure out, but seem to always be the same for the same verson of Lanschool. For 5.x and the low 6.x's the 1st byte here should be 00 for 6.5 and some others it should be DF in hex. The other 2 seem to always be the same. |
<br><br> | <br><br> | ||
| - | The data area is data for that | + | The data area is data for that command, some commands do not need this, for example, black all screens. |
<br><br> | <br><br> | ||
| - | The log area is where | + | The log area is where Lanschool puts the name of your computer and then your account username. This area also has a lot of useless 00 bytes that just take up space. |
<br><br> | <br><br> | ||
| + | |||
==Application of the packet== | ==Application of the packet== | ||
| - | The | + | '''Note:''' This application will not work with new versions of LanSchool as the '''flaw was fixed in version 7.0.''' |
| + | |||
| + | The following is a very simple Java application that will take advantage of the above information to black screens for the demo version of 6.5 of Lanschool only on the computer that you are using. To send it to all computers in a network you would need to use a destination mask that broadcasts to a subnet. | ||
<br><br> | <br><br> | ||
<code> | <code> | ||
| Line 59: | Line 158: | ||
}</code> | }</code> | ||
<br><br> | <br><br> | ||
| - | Note that for lesser verson of | + | Note that for a lesser verson of Lanschool, you would have to chage the 0x3f to 0x00 and possibly 0x02 to 0x01 or another number. Also, this is set to the demo channel 0xff and if you wanted to send to a real verson, then you would have to set it to 0xChannelNumberInHex. |
<br><br> | <br><br> | ||
==LanSchooled== | ==LanSchooled== | ||
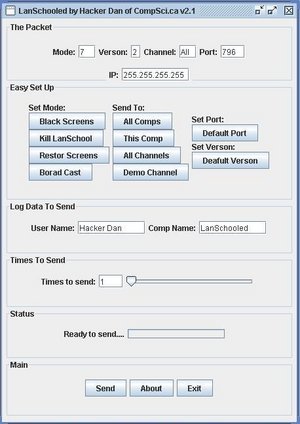
| - | + | [[Image:Lanschooled.JPG|thumb|300px|LanSchooled Screen Shot]] | |
| + | '''Note:''' "LanSchooled" is the name of the proof of conspect program to demonstrait a '''security flaw in LanSchool witch has since been fixed'''. "LanSchooled" should not be confused with the software it tried exploited, LanSchool."LanSchooled" in no way is ment to replace or do the same thing as LanSchool and should not be used as such, in fact "Lanschooled" does not work at all now that LanSchool has been updated. CompSci.ca nor Hacker Dan support "LanSchooled", sell it, or give advice on how to use it. | ||
| + | |||
| + | I used all this knowledge to make a point-and-click Lanschool hacking tool that can help you understand how the attack works. Remember that this is only for educational use and should not be used for evil purposes. I therefore take no responsibility for what you do with it. With that aside, I only tested it on the demo verson but i would like to hear from people who got it to work on other versions. | ||
<br><br> | <br><br> | ||
===How to use=== | ===How to use=== | ||
| - | The top frame shows the packet that will be sent, you can use the easy set up | + | The top frame shows the packet that will be sent, you can use the easy set up buttons below it to set the packet to do what you want. The times bar will let you say how many times that you want to send out the packet. |
<br><br> | <br><br> | ||
| - | + | Setting the channel to "ALL" will send to all possible Lanschool channels, including the demo one. Seting the version to "9" will send verson 2, but with 0x00 rather then 0xdf. Setting to "2" will send verson 2 but with 0xdf. All other verson numbers send their respective verson and 0x00. | |
<br><br> | <br><br> | ||
| - | The log info lets you set what | + | The log info lets you set what you want the name and computer name to be in the registry logs of the computers affected. I would strongly recommend that people do not expoit this to get others in trouble since that is morally wrong. |
<br><br> | <br><br> | ||
| - | You | + | You must hit send to transmit the packet. The easy set up buttons just configure the packet that you are going to send. |
<br><br> | <br><br> | ||
| + | |||
===Where to get=== | ===Where to get=== | ||
| + | '''Note:''' "LanSchooled" does not work since the '''flaw was fixed in v7.0''' and is ONLY here for historical reffernce. '''It won't work''', and it won't do anything. | ||
| + | |||
*Latest Versons of files: http://compsci.ca/dan/LanSchooled/ | *Latest Versons of files: http://compsci.ca/dan/LanSchooled/ | ||
*Sorce Code: http://compsci.ca/dan/LanSchooled/LanSchooled.java | *Sorce Code: http://compsci.ca/dan/LanSchooled/LanSchooled.java | ||
Latest revision as of 01:05, 20 August 2008
NOTE: This page details a proof of concept exploit of the LanSchool program which no longer works (since versions 7.0 and up). CompSci.ca and Hacker Dan do not support, condone or recommend the use of it in real life (So don't send us e-mails asking how to get it working or how to hack your schools network). Also since this exploit was found and LanSchooled was created, LanSchool has fixed the potential security hole described on this page. CompSci.ca and Hacker Dan will not help you exploit new versions of the software so do not e-mail us asking how. All information is provided as is and is the sole option of Hacker Dan and we are by no means responsible for how you use it or the effects it may have on you, your computer or anything that happens to you as a result of reading this page or using the software on and linked to from it.
Disclaimer: The content of this page is only the opinion of Hacker Dan and those who edit its content. Nothing on this page should be taken as fact with out checking the validity of the claim.
Contents |
What is LanSchool
LanSchool is type of monitoring program that is used by many school boards in Ontario to keep an eye on their students as well as controlling one or all computers in a given lab. It is seen by some as another example of the school boards spending money on software that they could get for free, with the free version even being of higher quality. Early versions LanSchool had a critical flaw in its design which caused the security hole mentioned below (which is now fixed in versions 7.0 and up).
The LanSchool website: http://www.lanschool.com/
The Story
Note: LanSchool has since updated there software and fixed the security issue talked about on this page in the below story. The bellow is solely the opinion of Hacker Dan and should not be taken as anything but just that.
The Story as told by Hacker Dan:
During Grade 12, I changed schools, and the new school that I went to had substantially better computing facilities. I thought this was a good thing, but after playing around for a bit, I noticed a little green icon in the system tray that did not seem to do anything. Looking in to this, I found out that it was a program named LanSchool (http://www.lanschool.com/). What is LanSchool you ask? The name makes it sound innocent enough, maybe something to help students? Well, it may have started out that way but what it has become is basically a Trojan horse program for teachers to use to watch everything that you are doing (inducing watching your screen) as well as giving them the ability to control your computer or all computers in the lab at the same time. As usual, the school board decided to spend money on something they could get for free and got a crappier version than what they could have got for free.
So I started looking in to LanSchool more and found a demo version on their site. This demo version could not interact with real versions that the school used and would not allow students to do any damage. 1st, I looked in to how it used the registry of the computers that it was on, and found that every time the teacher application sent a command to the student versions it recorded which windows user sent the command, the computer name of the computer that they were on and the time in all registries of every computer on the network. This meant that finding a full version of the software, although not hard, would end you up in a lot of trouble unless you brought your own computer to school and even then still could.
So I began to look at the packets it was sending and to my shock they were UDP and not TCP and they had no encryption or coding to them at all. This means that it is extremely easy to spoof the packets. So I quickly wrote up a simple java program to test out my theory. After some time and experimentation, I decoded what most of the packets meant and was able to control the demo version of LanSchool. After looking more at the packets, I noticed that the differences between the demo version and the real version was that the demo version uses only one channel that is never used by the real version. So it was simple a matter of changing the channel byte to a real channel in the packet to get it to work with most, if not all, versions of LanSchool. Also this allowed me to make the registry logs say what ever I wanted, including blaming other students for the hack.
Now being the nice guy that I am, I emailed my findings to LanSchool and suggested several ways to fix this exploit. There responses basically said that they would rather spend their time and effort enforcing the rules of the school and the law than fixing their program. They even made threats of legal action as well as suspensions that I could get were I to use this program. So next, I went to my school and actually demonstrated (with their permission) the exploit and how insecure the product was. Again, nothing happened as a result of my efforts, so a month later, I published how the system worked on compsci.ca.
It is now almost 2 years later, so I have rewritten my hack so anyone, even script kiddies can use it, even with a nice GUI and everything. My hope is that by doing this, I will teach people why programming software in the same way that LanSchool has been written is bad from a security and integrity viewpoint and to encourage the school board to buy (if they must use such software) better software from companies that know what they are doing and are willing to keep with the times. BTW, LanSchools website still claims that there are no known bugs with LanSchool.
Update: LanSchool fixed the security issue on May of 2007 and tried to contact Hacker Dan at this time, however due to a mix up with e-mail addresses this news was not received in till August 2008.
Communications with LanSchool
Feb. 26th, 2006
To: LanSchool
From: Hacker Dan
|
Hello, I am writing to let you know that you have a security flaw in your software, LanSchool v6.5. As with past versions of LanSchool, the system is not secure and uses a communication mechanism that allows for manipulation by anybody on a network whether they have the teacher version of the software installed or not. This becomes even more concerning when you see that this allows the exploiter to manipulate logs that are stored in the registry to what ever they want by manipulating communication appropriately. This would allow some students to exploit the network and then make it look like another student committed the attack from what ever computer they chose.
|
May of 2007
LanSchool tried to contact Hacker Dan when version 7.0 was released and fixed the security hole, however the messages never made it to him due a mix up with e-mail addresses.
August 5th, 2008
Beliving that Hacker Dan has ignored there messages in 2007, LanSchool sent the fallowing legal threat to CompSci.ca: http://compsci.ca/blog/wp-content/uploads/2008/08/lt-d-servos.pdf
Tony, posted a copy of the letter to the CompSci.ca blog with his commentary: http://compsci.ca/blog/lanschool-threatens-compscica-with-legal-actions/
August 5th to 7th
Internet drama ensues as the blog post makes Reddit and users and friends of CompSci.ca E-mail LanSchool.
August 7th, 2008
Hacker Dan and CompSci.ca send there official reply: http://compsci.ca/~dan/LT%20Dana%20Doggett.pdf
Dana Doggett of LanSchool replys:
|
Dan,
I’m glad I’m finally talking to you directly. I’m assuming my older e-mails must have gone to a bad address. Data Stream Encryption was one of the main features of LanSchool v7.0 in May of 2007. I e-mailed you when that shipped but I guess it never got through. I feel confident that if we had been able to communicate better, this would never have gone this far.
I’m fine with the four points you listed in your letter, with one modification. Since I fixed this in v7.0 of LanSchool I would like #2 to state that the “potential security flaw” was fixed in v7.0. Since I added that feature specifically for you, I don’t see that as too much to ask.
If you will agree to that clarification, we will instruct our attorney that the issue has been resolved.
My background is in programming, not public relations. I’ve obviously handled this poorly. Were I able to re-run this entire scenario, I would have been MUCH more proactive from the very start. Please accept my apologies and know that when this sort of thing occurs in the future, hopefully I’ll have learned and do it better.
Sincerely, Dana Doggett |
CompSci.ca makes the changes.
Hacker Dan's reply:
|
The changes (with your modification to #2) have been made to the pages in question. Also tony will be updating his blog post, stating that the issue has been resolved and was likely due to a miscommunication, in the next few days. If i had know of your attempts to contact me, i would have likely suggested and made the changes at that time. I am glad this matter could be resolved reasonably with an agreement by both sides and i hope any dealings between us in the future will be positive. Sincerely, Dan |
August 19th, 2008
Tony, after finishing his exams, finally writes a followup post to the above. http://compsci.ca/blog/legal-status-update/
The Packet
Note: Lanschool's packet was changed in v7.0 in May 2007 and added Data Stream Encryption which fixed the potential security flaw.
This is what the UDP packet looks like:
Mode | Version | Channel |00 or DF |DA | D1| ___data here__|__log info__|
Mode is basically the command that you are send. So far, I have found a lot of them. Here are some examples:
- 00 - Start broadcast of screens
- 04 - Restore computer screens
- 07 - Black all screens
- 08 - Unload Lanschool or just make it lock.
The verson corresponds to the verson of Lanschool that you are running. Versons 5.x seem to like 01, 02 seems to be for 6.x
The channel area is prity simple, it is the channel number. The demo verson uses channel FF in hex or 255 in decimal.
The next 3 bytes are kind of hard to figgure out, but seem to always be the same for the same verson of Lanschool. For 5.x and the low 6.x's the 1st byte here should be 00 for 6.5 and some others it should be DF in hex. The other 2 seem to always be the same.
The data area is data for that command, some commands do not need this, for example, black all screens.
The log area is where Lanschool puts the name of your computer and then your account username. This area also has a lot of useless 00 bytes that just take up space.
Application of the packet
Note: This application will not work with new versions of LanSchool as the flaw was fixed in version 7.0.
The following is a very simple Java application that will take advantage of the above information to black screens for the demo version of 6.5 of Lanschool only on the computer that you are using. To send it to all computers in a network you would need to use a destination mask that broadcasts to a subnet.
public class LanHack
{
public static void main(String args[])
{
try
{
InetAddress ipaddr=InetAddress.getByName("120.0.0.1");
DatagramSocket mysocket=new DatagramSocket();
byte sendbuf2[] = {(byte)0x07,(byte)0x02,(byte)0xff,(byte)0x3f,(byte)0xda, (byte)0xd1};
DatagramPacket sendPacket2 = new DatagramPacket( sendbuf2, sendbuf2.length, ipaddr, 796);
mysocket.send(sendPacket2);
}catch(Exception e){}
}
}
Note that for a lesser verson of Lanschool, you would have to chage the 0x3f to 0x00 and possibly 0x02 to 0x01 or another number. Also, this is set to the demo channel 0xff and if you wanted to send to a real verson, then you would have to set it to 0xChannelNumberInHex.
LanSchooled
Note: "LanSchooled" is the name of the proof of conspect program to demonstrait a security flaw in LanSchool witch has since been fixed. "LanSchooled" should not be confused with the software it tried exploited, LanSchool."LanSchooled" in no way is ment to replace or do the same thing as LanSchool and should not be used as such, in fact "Lanschooled" does not work at all now that LanSchool has been updated. CompSci.ca nor Hacker Dan support "LanSchooled", sell it, or give advice on how to use it.
I used all this knowledge to make a point-and-click Lanschool hacking tool that can help you understand how the attack works. Remember that this is only for educational use and should not be used for evil purposes. I therefore take no responsibility for what you do with it. With that aside, I only tested it on the demo verson but i would like to hear from people who got it to work on other versions.
How to use
The top frame shows the packet that will be sent, you can use the easy set up buttons below it to set the packet to do what you want. The times bar will let you say how many times that you want to send out the packet.
Setting the channel to "ALL" will send to all possible Lanschool channels, including the demo one. Seting the version to "9" will send verson 2, but with 0x00 rather then 0xdf. Setting to "2" will send verson 2 but with 0xdf. All other verson numbers send their respective verson and 0x00.
The log info lets you set what you want the name and computer name to be in the registry logs of the computers affected. I would strongly recommend that people do not expoit this to get others in trouble since that is morally wrong.
You must hit send to transmit the packet. The easy set up buttons just configure the packet that you are going to send.
Where to get
Note: "LanSchooled" does not work since the flaw was fixed in v7.0 and is ONLY here for historical reffernce. It won't work, and it won't do anything.
- Latest Versons of files: http://compsci.ca/dan/LanSchooled/
- Sorce Code: http://compsci.ca/dan/LanSchooled/LanSchooled.java
- Class File: http://compsci.ca/dan/LanSchooled/LanSchooled.class
- Excutbale Jar: http://compsci.ca/dan/LanSchooled/LanSchooled.jar
- EXE Verson: http://compsci.ca/dan/LanSchooled/LanSchooled.exe